Integrating SSO with Threatcop Admin
- Log in to the portal using your credentials.
- From the left-hand navigation menu, click on “Directory” (located under the “Other” section).
- Click on “Integrations”, also located under the “Other” section.
- In the SSO section, click on “Integrate”.
- On the top-right corner (just below the user profile), click on “Add IDP”.
- The required SSO configuration details will now be visible.
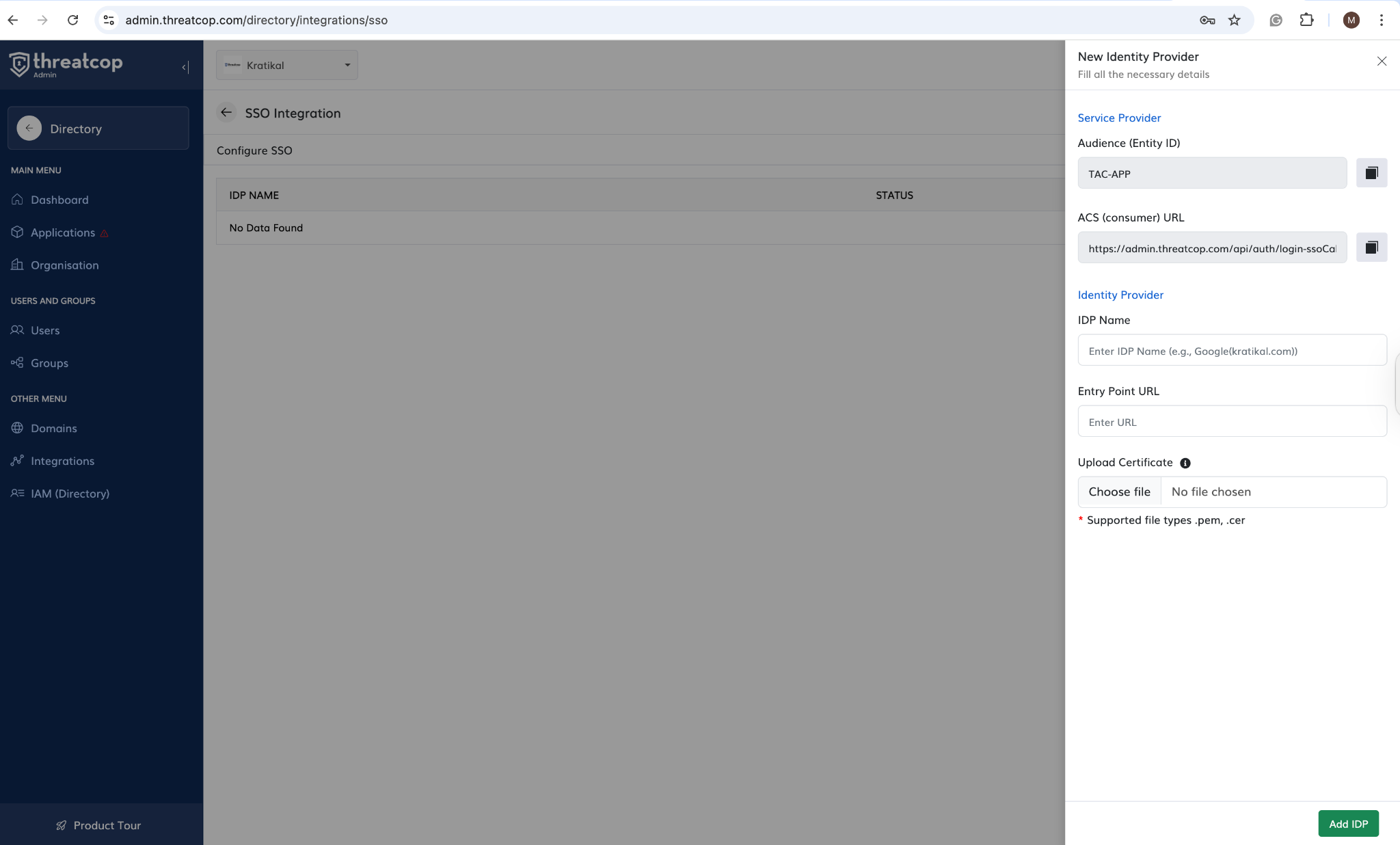
Related Articles
How to configure SSO Login With G-Suite In TLMS
Background Single sign-on (SSO) is an authentication method that enables users to securely authenticate with multiple applications and websites by using just one set of credentials. User Flow Diagram Steps to configure SSO (G- Suite) Step 1: Navigate ...
How to whitelist Threatcop in GSuite
Whitelisting IP Address This process allows emails from specific IP addresses to bypass spam filtering. Step 1: Go to https://admin.google.com/ Step 2: Select Apps -> Google Workspace -> Gmail -> Spam, Phishing and Malware Step 3: Select your ...
How to Whitelist Threatcop by Email Header in Google Workspace
Whitelist by Email Header in Google Workspace If your organization uses Google Workspace, you can ensure delivery of Threatcop’s simulated phishing emails by whitelisting them using email headers. This is done by applying a Content Compliance rule ...
How to Whitelist ThreatCop in Mimecast
Whitelisting Threatcop in Mimecast 1. Inbound Email Policies Step 1: Create a Permitted Senders Policy Path: Administration → Gateway → Policies → Permitted Senders → New Policy Configuration: - Policy Narrative: Threatcop – Permitted Senders - ...
Whitelisting Threatcop in Cisco IronPort and Bypassing Outbreak Filter Scanning
Whitelist TSAT in Cisco Ironport If you’re using Cisco IronPort for spam filtering, you might want to whitelist/bypass certain sources to ensure important emails and notifications get through to Threatcop’s to end users. This guide will walk you ...